A communication device on the ground as Lebanese army forces prepare to destroy it in a controlled explosion. September 19, 2024. (Photo: CFP)
Thousands of handheld radios and pagers used by Hezbollah were detonated across Lebanon this week, killing dozens and wounding thousands.
The attacks, according to Lebanon's armed group Hezbollah, were carried out by Mossad, Israel's spy agency.
This week's explosions have also deepened concerns about the scope of potentially compromised devices, particularly after such bombings have killed or injured so many civilians.
How the communication devices become bombs?
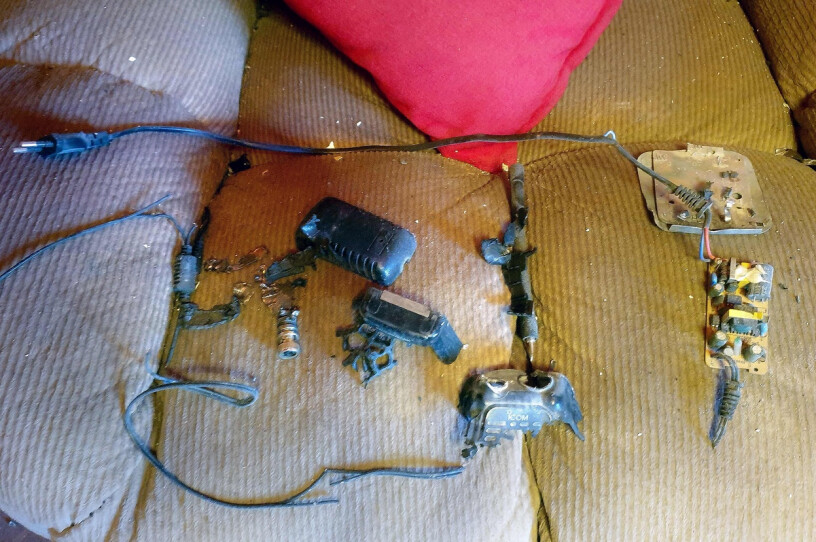
The remains of an exploded radio device inside a house in Baalbek in eastern Lebanon. September 18, 2024. (Photo: CFP)
Several reports suggest that the pagers involved may have been manufactured by Gold Apollo, a company based in Taiwan, China.
However, the company said Wednesday it had authorized the use of its brand on the AR-924 pager model — but that a Budapest, Hungary-based company called BAC Consulting KFT produced and sold the pagers.
Current theories are that the pagers were tampered with, possibly by adding explosives such as pentaerythritol tetranitrate (PETN) or C4, before they entered Lebanon.
"The first step is to interrupt the supply chain and gain access to the device," explained Dr. Suresh Ramasamy, Chief Research Officer at Malaysia's Center for Advanced Computing & Telecommunications. "Then, modifications can be made to embed explosives in the pagers."
Ramasamy told GDToday that the next challenge is triggering the device. In this case, it could have been done by tapping into the pager network and sending a broadcast message, which would activate the detonator.
"The explosives might have been triggered either via a cell tower or from an aircraft capable of hacking into wireless networks," Ramasamy added.
Ramasamy also expressed concern that some tampered pagers could have been sold outside Lebanon, increasing the risk of accidental detonation. "If someone unintentionally sent a trigger message, another explosion could occur," he warned.
Can mobile phones be weaponized as well?

A communication device on the ground as Lebanese army forces prepare to destroy it in a controlled explosion. September 19, 2024. (Photo: CFP)
The short answer: yes.
Ramasamy told us that any device with a battery and radio frequency capabilities, including mobile phones, laptops, and cars, could potentially be turned into an explosive.
"The common factor is the battery, which provides the charge needed to set off an explosive," Ramasamy explained. "Beyond that, a radio frequency interface allows a signal to be received, triggering detonation."
Some experts argue, however, that large-scale attacks using mobile phones would be more difficult to carry out.
"Modern smartphones have various security protocols that make them harder to breach on a mass scale" said Haris Ali, a cybersecurity analyst from Pakistan, in an interview with GDToday.
The reality is that the fear of exploding electronic devices is spreading among civilians in Lebanon and beyond.
According to AFP, some Lebanese citizens, gripped by panic, have begun throwing away power banks or sleeping with their mobile phones in another room.
"Now that even common devices are being weaponized," Ramasamy said, "we're likely to see heightened paranoia in some communities."
How dangerous is supply chain compromise?

(Hezbollah members carry the coffins of two of their comrades who were killed on Wednesday when a handheld device exploded. Sept. 19, 2024. (Photo: CFP)
The speculation that these exploding devices were tampered with before being delivered to Hezbollah members in Lebanon raises serious concerns over supply chain compromise.
"It is a serious concern for national and global security," warned Ali.
Ali explained to GDToday that it can lead to disruptions in essential services, economic loss, and threats to public safety when critical components or services are tampered with or infiltrated.
Ramasamy anticipates there will be a more stringent approach taken by organizations and countries on imported devices.
"Now we might see every single device being x-rayed to ensure that if it's a lithium battery, there are no C4 or other explosive materials in the device," said Ramasamy.
"Countries should invest in robust cybersecurity protocols, promote supply chain transparency, and encourage diverse sourcing for critical materials," Ali suggested.
Milad Haghani, a supply chain expert at the University of New South Wales, told Al Jazeera he expects a "widespread reckoning," prompting companies to tighten their supply chain security protocols.
Big smartphone manufacturers like Apple, Samsung, Huawei, Xiaomi, and LG are considered less vulnerable to supply chain tampering compared to smaller companies due to their heightened attention to security.
"Consumers may gravitate towards trusted brands," Ali told GDToday, "supply chains may evolve, with businesses prioritizing local suppliers and investing in security solutions."
Author | Xachary, Zhou Jing (intern)
Photo | CFP
Editor | Nina, Steven, James